One might think that discussions about “big data” would start and end in cyberspace. The fact of the matter is that even data must be stored in physical locations within physical hardware. Those physical assets need to be protected as securely as the data they contain. There are two directions from which threats to physical security can arise — inside and outside. Threats from the outside are often easier to deal with threats than threats from the inside because the number of potential breach attempts is lower and the vulnerabilities are generally better known. Internal physical security threats, however, generally make it onto analysts’ lists of top risks to cloud computing. At a recent conference, Marlin Pohlman “noted that No. 3 on the Cloud Security Alliance’s ‘Top Threats to Cloud Computing’ list is malicious insiders.” [“Why physical security matters, even in the cloud,” by Thomas J. Trappler, Computer World, 26 October 2011] Trappler, director of software licensing at UCLA and a nationally recognized expert in cloud computing risk mitigation, writes, “This serves as a good reminder that old-fashioned physical security issues require a lot of attention when you’re considering a cloud service provider.”
Jeff Beckman, a solution manager at Cisco, ranks “user access control” as the number four security threat on his Top 5 list. [“The Top 5 Security Risks of Cloud Computing,” Cisco Blog, 3 May 2011] He writes:
“Data stored on a cloud provider’s server can potentially be accessed by an employee of that company, and you have none of the usual personnel controls over those people. First, consider carefully the sensitivity of the data you’re allowing out into the cloud. Second, follow research firm Gartner’s suggestion to ask providers for specifics about the people who manage your data and the level of access they have to it.”
Trappler agrees with Beckman and asserts that “it’s important to vet the physical security of a cloud provider’s data centers.” He discusses “some of the key issues to investigate” when searching for cloud storage provider:
“Security policy. A policy typically details the mechanisms that the vendor has in place to prevent security breaches. An incident response plan typically details steps the provider will take should a breach occur. If the vendor has such documents, carefully review them. If it doesn’t, that’s a big red warning flag.”
Although the primary focus of a contingency plan dealing with security breaches is likely to be on hacking breaches, it should also deal with unauthorized entry onto the premises. Unauthorized entry breaches, however, can also come from inside an organization. That is why Trappler’s next issue deals with access control. He writes:
“Access Controls. Does the cloud provider have physical access controls in place to ensure that only authorized personnel are able to access the IT infrastructure on which your data is stored and processed? Ask the following questions:
• Are the data centers in nondescript facilities?
• Do those facilities have security guards, gates and checkpoints?
• Do they have video surveillance systems?
• Does the vendor use intrusion-detection technology?
• Does it use multifactor authentication?
• Does it have a need-based access policy, with access rescinded if a user’s need changes?
Even if adequate access controls are in place, Trappler reminds us that not everyone working in a facility necessarily has your best interests at heart. That is why he recommends that background checks be conducted. He writes:
“Background checks. Does the cloud provider conduct background checks on everyone who has access to its infrastructure and your data? This can prevent malicious insiders from getting inside in the first place. Additionally, you should determine if the cloud provider requires all staffers to receive training that covers the issues pertinent to data security and the provider’s own security policies.”
I’ve read study results that assert that the greatest risk to most IT systems come from intentional and unintentional actions by personnel within an organization. That is why Trappler stresses the importance of training and procedures. He then recommends going a step further by segregating duties. He writes:
“Segregation of duties. Does the cloud provider distribute key tasks among multiple employees? This can help ensure that no single person is able to execute an unauthorized or inaccurate end-to-end transaction and go undetected. And if there are malicious insiders, the practice of distributing tasks among various people will make it harder for them to get away with anything.”
You want your service provider to be paranoid when it comes to protecting your data. Things get trickier if third parties have access to your data. Trappler explains:
“Third-party adherence. If the cloud provider works with third parties, does it contractually require that those third parties understand and abide by the same security policies that apply to the provider’s employees? Also, does the provider have processes in place to monitor the activities of third parties to ensure compliance? This can help prevent a malicious third party from becoming a malicious insider.”
Trappler recommends making security guarantees a part any contract. He concludes:
“As always, you need to address these issues in the contract. If the cloud provider’s security policy and incident response plan pass muster, then simply attach those documents to the contract and designate them as the cloud provider’s minimum security requirements. If the policy and plan are lacking, you can address any shortcomings with additional corrective language in the contract. Following this process and codifying requirements in the cloud service contract is the best way to effectively minimize risks in the cloud.”
Nick Coleman agrees that security remains the single greatest concern that companies have about cloud computing. He writes, “The big questions with cloud security boil down to: Where is my data? Who will be able to access it? And, how will I be able to maintain oversight and governance?” [“Securing The Cloud: Questions and Answers,” Wired Cloudline] He continues:
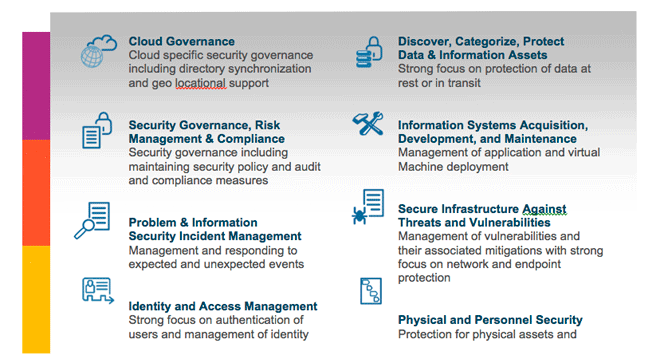
“In looking at security, the fundamentals still apply. Building security involves three essential considerations: Have we designed security into how we build the cloud? Have we understood this in the context of what we are trying to do? Have we got security running for these cloud environments? To ensure we are communicating our approach we developed the cloud security reference model to help achieve this. This reference model [see attached figure] covers eight categories ranging from cloud governance, security, and risk and incident management to infrastructure protection and personnel and physical security.”
I like the framework because it addresses people, processes, and technology — three things that must always be kept in mind in any organization. Coleman indicates that “the reference model also allows for setting expectations about what the cloud provider would do and what the customer is expected to do.” That’s a good point. Without proper procedural practices by customers, they could actually end up making their own data vulnerable. Coleman concludes:
“In summary over the past several years, security concerns surrounding cloud computing have become the most common inhibitor of widespread usage. This often translates to where is my data, who will be able to access my data, and how will I maintain oversight and governance? Each cloud model has different features which changes the way security gets delivered which also changes the way we look at security governance and assurance. Determining your desired security posture [allows you tailor the] cloud in such a way that the new risks can be managed in a rapidly changing landscape.”
Whether you manage your own data, access control, and other layers of security, or outsource those responsibilities to a cloud provider, you must be aggressive in implementing security policies. My company, Enterra Solutions®, believes that attribute-based access control (ABAC) is the best way to facilitate information sharing policies within an organization as well as sharing information outside the organization (e.g., with business partners, regulatory bodies, law enforcement). It is a scalable framework that implements security policy from the top down but leaves the organization that owns the data in charge of who has access to it and how it is shared across a federated domain. We have applied this framework to physical security surveillance systems so that critical infrastructure enterprises can automatically provide first responders access to closed-circuit television (CCTV) video so that they can incorporate “live data” as they respond to an incident. Our framework ensures compliance with the enterprise security policies and Information Sharing Governance Plan and validates that the latest rules are applied to the specific situation and data being shared.
Today, sharing enterprise data is easier and has more value to your business if used in a real-time vice an archived approach (e.g., feeding a live video of a robbery to the police is more useful in protecting your property than giving them your surveillance tape after the fact). However, the complexity of sharing such information even with law enforcement or other government agencies probably requires a relook at your information sharing governance structure and enterprise security policies. Some sharing is driven by regulations and some by your business policies, either way; your governance framework for information sharing should be policy-driven so that you know all of your bases are covered. Our ABAC framework enables this governance model for the most granular level of data (e.g., for the CCTV video, it could be a specific date/time archive video from a specific camera). This framework is applicable to any cloud offering where complex access control rules, federated users groups, multiple systems and applications, large data sets, and dynamic situations are present.