When the topic of supply chain security is raised, the two sources of insecurity that are mentioned most frequently in the press are terrorists and pirates. In two previous posts on this topic (Terrorism and the Supply Chain and Supply Chain Resilience and Supply Chain Security), I focused mostly on terrorism. The fact of the matter is, however, that terrorism and piracy aren’t the greatest sources of disruption or loss in the supply chain. They draw the headlines because people fear them and fear sells papers. Another reason that terrorism and piracy grab headlines is because people expect governments to deal with them. If a company suffers a loss because its IT system is hacked or because it is duped by someone who forged documents, most people consider that a “personal problem” rather than a national security problem.
Cliff Holste, Supply Chain Digest‘s Material Handling Editor, asserts that supply chain cybersecurity is one area that companies simply can’t afford to overlook. Last February he penned an article entitled “Logistics News: The Question Is Not ‘IF’ Your System Will Be Hacked Into, But ‘WHEN’.” [25 February 2011] In that piece, he wrote:
“Computing system security is a huge problem and … security is everyone’s business, not just your IT departments. That’s a point worth taking the time to contemplate, because security is like a chain and those individuals bent on causing trouble will find and exploit the weakest link. ‘The ZeuS Compromise’ may sound like a great movie, but it’s actually a newly uncovered, massive hacking network – and it’s a doozy. According to a recent news report, it has already affected more than 74,000 PCs in 2,400 business and government systems around the world. The computers were infected with spyware called ZenS, which is freely available on the Internet. But worse, the security analysts who detected the underground network believe the criminals behind it aren’t even after money. Instead they have built a secret underground network to rent out to gangs, cybercrooks, and even rogue governments. The threat is global and constantly growing. Toralv Dirro, a security strategist with McAfee, points out that there are ‘a few thousands’ of such networks (referred to as botnets). He said that, ‘With 75,000 machines, The ZeuS Compromise is a big botnet, but we’ve seen much bigger, unfortunately.’ According to Dirro, around 4 million new computers are being added to these botnets each month. Companies need to be aware that not just consumer machines but users inside corporate networks are becoming part of these networks. He hopes these latest revelations inspire companies to become more proactive about protection.”
Holste points out that cybersecurity must be an important part of any company’s business continuity plan. “A key objective of any security system,” he writes, “is to ensure that business processes continually function.” Security in general must be part of any business continuity and disaster recovery plan. In another article, Holste writes:
“Security, whether you think it’s too much or not enough, is front and center on everyone’s mind these days, and for good reasons. If there’s one crucial point to be made about security, it is that it can’t be ‘security-light.’ You can’t have the illusion of security, as in mounting cameras on your dock that you never turn on or view. Nor can there be just the perception of security, as in hand searching through carryon bags, and removing miniature pocket knives that contain a scissors, nail file and plastic tooth pick (I really hate having to give up such a handy, harmless travel aid!). Systems with the function of security must be real.” [“Good Security Is All About Planning, Execution, And Paying Attention to Details,” Supply Chain Digest, 10 February 2011]
A good security consultant can help your business determine what it needs to ensure robust security. Every business is different so trying to present a one-size-fits-all plan would be fruitless. I would, therefore, like to spend the remainder of this post discussing more general security issues, including terrorism, that continue to find their way into the media. Because international supply chains are affected by security policies and circumstances in different countries, supply chain professionals must be vigilant. They don’t want their company or their processes to be the weak link in the chain that permits the unthinkable to happen. On the other hand, they don’t want security procedures to be so onerous that they become a burden whose cost can’t be borne. We all know that security doesn’t come free; but Holste insists that it is a cost that must be covered [“Supply Chain Security – A Cost We Must Bear,” Supply Chain Digest, 19 January 2011]. He writes:
“Security of the supply chain is an important concern for all trading companies small or large, domestic or international. … Distributors, especially those with global reach, must become proactive in security planning. The increasing frequency of terrorism as well as security breaches occurring abroad and domestically has driven awareness to new levels. … Supply chain security starts with an organization’s developing a security awareness culture. … Employees at all levels should be educated on potential threats to the supply chain and provided the means to counter these threats. Conversely, organizations should solicit input from employees on vulnerabilities they see. Periodic security inspections should be conducted to ensure all within an organization are in compliance with security measures. … Vulnerabilities in the supply chain cannot only cost a company monetary and human resources, but they can threaten the security of the nation. A well-coordinated and effective effort protecting our supply chains is a cost we must bear.”
The challenge for supply chain professionals involved is that they deal with enormous quantities of goods. So, they not only have to deal with daily security challenges (like pilfering, theft, and fraud), they have to deal with consequences of potential challenges (like piracy, terrorism, and natural disasters). When assessing risk, analysts normally begin by looking at two factors: the likelihood that an event will occur and the potential consequences if it does. Often events that have the highest likelihood have the lowest consequences and events having the lowest likelihood have the highest consequences. That presents a real conundrum for planners. Holste has some thoughts along those lines as well. In the second of his articles noted above, he writes:
“Sometimes, good security is no more difficult than actually executing the plan. Maybe that’s all that needs to be done; just develop a good plan and actually execute it. Attend to the details! We’ve been sloppy in the past, taking for granted that we are immune to attack or that a few billion dollars in ‘shrinkage’ is an acceptable loss. Now, a new report from FreightWatch International finds that truck cargo thefts in the US increased substantially in 2009, just as they did in 2008. … Well, now we know better, but that doesn’t mean we need to go overboard to improve security. After the shoe bomber – everyone has to remove their shoes, which are then put through a scanner; and, after the recent Christmas Day underwear bomber – everyone will eventually have to submit to a full body X-Ray scan, and once on the plane, there will be no lavatory privileges the last hour of the flight. Does this really make it safer to fly? Maybe all we need in airports, at cargo ports, truck stops and freight terminals, in warehouses and DCs is to analyze our vulnerabilities, develop a plan to eliminate or protect those vulnerabilities, and effectively execute that plan. The key word is effectively.”
I don’t believe that Holste means to imply that creating and implementing an effective plan is an easy thing to do. It isn’t. In another article, the editorial staff at Supply Chain Digest lays out the enormity of the challenge in maritime shipping industry and the status of some of the government programs aimed at improving supply chain security [“The Complex World of Cargo Security and Government Programs and Standards,” 2 November 2010]. The article reports:
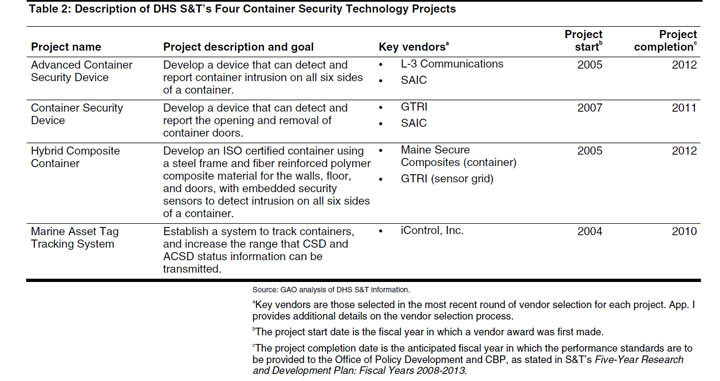
“Approximately 9.8 million cargo containers arrived at US ports in 2009, and just a fraction received much in the way of inspection, with a multiple-layer security protocol in place to protect security that primarily relies on trusted partners and identifying shipments that may be worrisome through receipt of advanced information about who is shipping what where. The US Customs and Border Protection (CBP) is responsible for administering container security and reducing the vulnerabilities associated with the supply chain. But, the report notes, ‘As it performs this mission, CBP maintains two overarching and sometimes conflicting goals—increasing security while efficiently facilitating legitimate trade.’ This is especially challenging given the number of players and touch points usually involved in cargo movement from some part of the globe into the US. In turn, to enhance container security, CBP has partnered with Dept. of Homeland Security’s Science and Technology (S&T) Directorate to develop performance standards and requirements that must be met by products to ensure they will function as intended relative for container security technologies. The report notes that in addition to a number of existing programs, there are four new programs involving new technologies and standards currently in some form of progress, as shown in the graphic below.” (Click to enlarge image.)
The article goes to note that work progresses slowly because of the complexities and tensions involved. The challenges involved in air cargo security aren’t quite as daunting as those facing the maritime arena, but they are nonetheless significant. [“Easing the Burden of Air Cargo Security Compliance and Reporting,” by Cindy Yamamoto, Logistics Viewpoints, 3 March 2011]. Yamamoto, the Senior Vice President for Product Strategy at Descartes, writes:
“While governments around the world have become increasingly vigilant about air cargo security and compliance, freight forwarders and air carriers have always understood that these are critical areas of concern. Increased demands in terms of visibility and reporting requirements have led to far more complex processes and, without the right technologies and tools in place, these processes can become alarmingly inefficient. Today, freight forwarders are grappling with a number of process challenges as they strive to meet the performance metrics that their customers demand. Many lack real-time visibility into the status of their cargo shipments. Further, since their customers are the owners of the underlying supply chain data, freight forwarders face challenges in accessing, filing and amending regulatory filings in a timely manner that is consistent with the important confidentiality concerns of regulators and the customer. This is further complicated by the fact that freight forwarders can carry an administrative cost burden of between $2 and $9 a shipment associated with filing critical documents, which means any errors, omissions or delays can become costly.”
Yamamoto goes on to suggest “some simple steps to address complex challenges.” Her “bottom line is that on-demand logistics management solutions provide an affordable and highly effective way for freight forwarders to address the increasing challenges of moving cargo across borders while ensuring customer satisfaction.” One the things that comes through clearly in all of these discussions is that improved information sharing is necessary to foster improved security throughout complex supply chains. The dilemma is that many stakeholders believe that increasing data sharing increases cybersecurity risks. Fortunately, there are new technologies that greatly reduce such risks (such as attribute-based access control and other secure information sharing techniques). As Holste asserts, however, good security starts with a good plan. It continues with good execution and attention to detail. I daresay that carelessness is the greatest risk that supply chains face.